Vulnerability Assessment
Many companies are aware of existing threats and defend only by a minimum of cyber defense mechanism, leaving really at risk corporate assets. For this reason it is appropriate to have experts in computer security, as Cleis Security, to protect your perimeter to attacks that could seriously threaten the company's assets.
Benefits
Our vulnerability assessment service is meeting the company's needs.
In fact it provides:
Identification of infrastructure vulnerabilities, allowing it to be aware of the decisions to be taken to limit the risk of a cyber attack.
Allowing greater commitments to the most important and sensitive areas, according to business priorities.
Our service
Cleis Security provides a vulnerability assessment service, using certified staff to provide a level of service and experience. The goal of our service is to defend better corporate perimeter from threats that can dent, interacting with the customer to understand the business priorities.
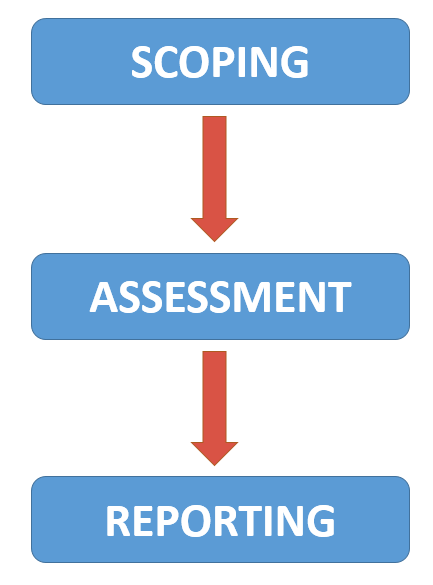
1. Scoping
Preliminarily we undertake an activity of working with IT professionals to define the limits of the infrastructure to ensure that the entire IT network, web applications and related services are included in the assessment, observing the defined business priorities.
2. Assessment
Obtained the scope of the assessment, the service that we will provide our team will see action through updated tool to scan defined perimeters, to determine the existence of vulnerabilities within enterprise systems.
3. Reporting
Finally, our assessment services include the presentation of a report as a feedback to the customer. This report will outline the state of the company, listing all the vulnerabilities in order based on their importance and ability to exploit.
To ensure efficient service, it is advised to run an assessment through our support twice a year.